As we build a society that resembles a machine, we can’t assume it will be one of loving grace.
I don’t subscribe to John Markoff’s idea that we can coolly decide the path forward. These decisions will be made in the heat of battle–state versus state, corporation versus corporation. Nor am I completely deterministic about the outcome. Miracles will intermingle with malice, and constant attention and intervention will be required to mitigate the latter.
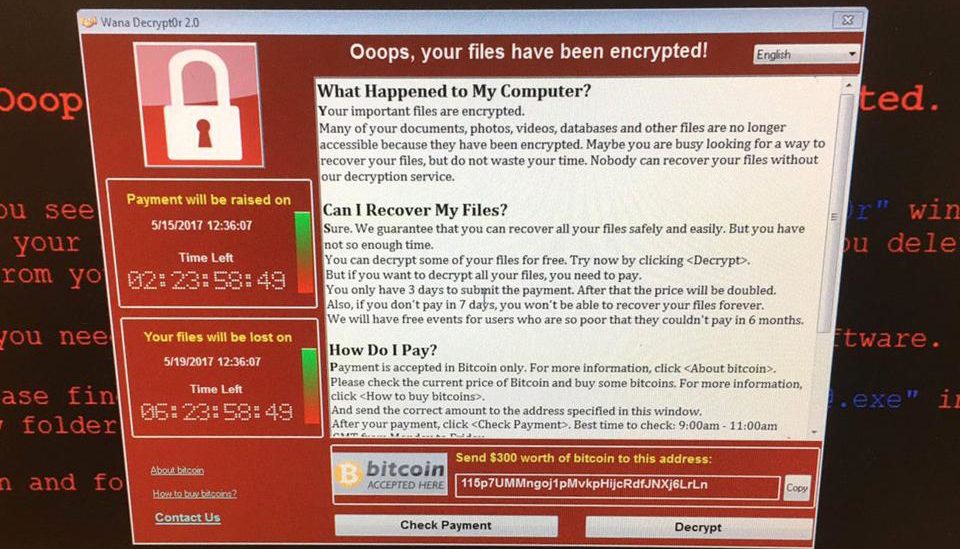
As today’s widespread, pernicious ransomware attack of European and Asian countries the globe reminds, a world in which everything is a computer–even our brains–is a fraught one.
The opening of a New York Times article by Dan Bilefsky and Nicole Perlroth:
LONDON — An extensive cyberattack struck computers across a wide swath of Europe and Asia on Friday, and strained the public health system in Britain, where doctors were blocked from patient files and emergency rooms were forced to divert patients.
The attack involved ransomware, a kind of malware that encrypts data and locks out the user. According to security experts, it exploited a vulnerability that was discovered and developed by the National Security Agency.
The hacking tool was leaked by a group calling itself the Shadow Brokers, which has been dumping stolen N.S.A. hacking tools online beginning last year. Microsoft rolled out a patch for the vulnerability last March, but hackers took advantage of the fact that vulnerable targets — particularly hospitals — had yet to update their systems.
The malware was circulated by email; targets were sent an encrypted, compressed file that, once loaded, allowed the ransomware to infiltrate its targets.
By then, it was already too late. As the disruptions rippled through hospitals, doctors’ offices and ambulance companies across Britain on Friday, the health service declared the attack as a “major incident,” a warning that local health services could be overwhelmed by patients.•